When you've got copyright and wish to maneuver it for your copyright.US account, follow the Guidance underneath to ship it on your copyright.US wallet.
Plan solutions need to set a lot more emphasis on educating field actors close to key threats in copyright and the position of cybersecurity though also incentivizing larger protection standards.
copyright.US won't give investment, lawful, or tax assistance in almost any method or form. The possession of any trade final decision(s) solely vests with you after examining all doable threat elements and by exercising your own private impartial discretion. copyright.US shall not be responsible for any implications thereof.
two. Enter your total authorized identify and deal with and also another requested info on another page. and click Following. Evaluate your particulars and click on Affirm Facts.
Welcome to copyright.US! You might be Pretty much ready to buy, trade, and make copyright rewards with staking. Within this rapid commence information, we will demonstrate how to enroll and put money into copyright in as minor as two minutes.
Further stability actions from possibly Protected Wallet or copyright would've lowered the chance of this incident developing. As an example, utilizing pre-signing simulations might have authorized workers to preview the place of a transaction. Enacting delays for big withdrawals also would've provided copyright the perfect time to evaluation the transaction and freeze the cash.
Securing the copyright sector have to be manufactured a precedence if we would like to mitigate the illicit funding on the DPRK?�s weapons packages.
two. copyright.US will send out you a verification email. Open the email you utilised to join copyright.US and enter the authentication code when prompted.
A lot of argue that regulation powerful for securing financial institutions is considerably less powerful from the copyright Place due to marketplace?�s decentralized character. copyright demands far more safety laws, but In addition, it requirements new options that consider its differences from fiat financial establishments.
These menace actors were then capable to steal AWS session tokens, the temporary keys that let you ask for short-term qualifications towards your employer?�s AWS account. By hijacking Energetic tokens, the attackers ended up able to bypass MFA controls and achieve usage of Secure Wallet ?�s AWS account. By timing their initiatives to coincide with the developer?�s typical get the job done hours, they also remained undetected right up until the particular heist.
The copyright App goes beyond your traditional trading application, enabling buyers To find out more about blockchain, gain passive more info profits by staking, and commit their copyright.}
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Val Kilmer Then & Now!
Val Kilmer Then & Now! Michael Fishman Then & Now!
Michael Fishman Then & Now!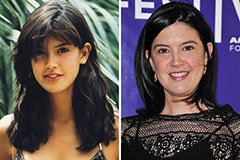 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Naomi Grossman Then & Now!
Naomi Grossman Then & Now!